EfficienIT’s Incident Response & Forensics Services in Arizona
The New Standard for Incident Response & Forensics in Phoenix, Scottsdale, and Chandler AZ
EfficienIT’s Incident Response & Forensics Services in Arizona setting the new standard for incident response & forensics services to keep your business safe and secure. With over 16 years of hands-on experience using the industry’s best tools for threat hunting and network analytics forensics
from SIEM systems like Splunk, IBM QRadar, ArcSight, and Elastic Stack to advance EDR systems like CrowdStrike Falcon, Carbon Black, SentinelOne, and more to deliver fast, precise results. we quickly spot, contain, and knock out cyber threats. Our goal? To minimize damage and stop future attacks so you can keep focusing on what you do best.
Whether you’re dealing with a data breach or cyber attack right now or just want to be prepared, we’ve got you covered. Our team works both onsite and remotely, providing the support and consultation you need in Phoenix, Scottsdale, and Chandler AZ.
At EfficienIT, we know the importance of a quick response. We build customized incident response plans, using best practices from frameworks like NIST and MITRE ATT&CK, to help you bounce back quickly from any cyber incident. Our experts are here to strengthen your defenses and keep your business running smoothly, no matter what comes your way.
Get peace of mind with EfficienIT’s new standard incident response and forensics services.
Let’s build a safer, more secure business together! contact EfficienIT online or call +1602-750-1083 us today.
What Are the Types of CyberSecurity Incidents?

A security incident could signal that your systems or data are at risk Many businesses miss these signs
- Insider Threats: Unusual data requests from employees outside their job scope.
- Phishing Indicators: Unexpected redirects or frequent pop-ups, suggesting phishing or malware.
- Anomalous Network Traffic: Irregular patterns in outbound traffic, which could mean data exfiltration.
- Configuration Changes: Unauthorized adjustments to system settings, exposing vulnerabilities.
- Account Anomalies: Unexpected password changes or user lockouts, pointing to potential account compromise.
- Hidden or Suspicious Files: Concealed files could indicate malware or unauthorized access attempts.
Injection Attacks
One of the most critical threats to network security, injection attacks involve hackers inserting malicious code into a vulnerable application. This can lead to unauthorized data access, data loss, and full control of a system. Businesses need to implement strong input validation and sanitization measures to protect against SQL, NoSQL, command, and LDAP injection attacks. EfficienIT provides expert consulting to identify and patch these vulnerabilities, enhancing your web application security
Phishing Attacks
A prevalent form of social engineering, phishing attacks deceive employees into divulging sensitive information by pretending to be a trusted contact or entity. These attacks often lead to data breaches and unauthorized account access. EfficienIT offers comprehensive training programs and security solutions to help businesses recognize phishing attempts and safeguard their sensitive data.
dvanced Persistent Threats (APTs)
APTs are sophisticated, long-term attacks where cybercriminals gain unauthorized access to a network and remain undetected to steal sensitive information or disrupt operations. These threats require a high level of vigilance and advanced security monitoring. EfficienIT helps businesses build robust defenses with continuous monitoring, threat intelligence, and advanced response strategies to detect and mitigate APTs quickly.
Denial-of-Service (DoS) Attacks
DoS attacks overload a network or server with excessive traffic, causing a shutdown and preventing legitimate users from accessing services. This can lead to significant operational downtime and reputational damage. EfficienIT implements advanced traffic management and network security solutions to mitigate DoS attacks, ensuring your network remains available and secure.
Credential Stuffing and Password Attacks
These attacks involve using automated tools to crack or reuse passwords across multiple sites, exploiting weak or compromised credentials. Protecting against these attacks requires strong password policies, multi-factor authentication (MFA), and regular security audits. EfficienIT provides businesses with comprehensive password management and MFA solutions to secure their systems against unauthorized access.
Malware Attacks
Malware, including ransomware, spyware, Trojans, and viruses, infiltrates networks through phishing emails, infected downloads, or compromised websites. These attacks can steal data, disrupt operations, or demand ransom payments. EfficienIT uses advanced malware detection tools and strategies to prevent and remove malware threats, keeping your network safe and secure.
EfficienIT’s advanced Incident Response & Forensics Services in phoenix Arizona
Emergency Incident Response
A cybersecurity breach can have a severe impact on your business and your customers, affecting everything from data integrity to your company’s reputation. That’s why it’s crucial to act fast when a breach occurs. At EfficienIT, our emergency incident response team is ready to step in immediately, helping you quickly assess the situation, contain the threat, minimize damage, and restore operations. Having a solid incident response plan in place is more than just a list of steps it’s a strategic asset, A well-prepared plan helps your team stay calm and respond effectively during a crisis, reducing panic and minimizing potential mistakes. This approach not only secures your business operations but also reinforces confidence among employees and customers, ensuring you bounce back stronger after an incident.
Proactive Incident Response
Threat hunting is all about being proactive and actively searching for hidden cyber threats that may already be lurking in your network. EfficienIT’s threat hunting assessment assumes that attackers have already breached your defenses and focuses on finding them quickly. Our team uses a blend of theory-driven investigations, advanced analytics, machine learning, and indicators of compromise to detect threats before they cause damage. By identifying threats early, EfficienIT helps businesses enhance their cybersecurity posture, reduce risks, and stay secure. Contact us today to learn how our proactive threat hunting services can protect your network from unseen dangers!
Cyberattack and Network Forensics
EfficienIT’s Cyberattack and Network Forensics services are designed to uncover the details of a cyber incident after it occurs. Our forensic experts meticulously analyze digital evidence to identify the source, method, and impact of a cyberattack. This process involves examining logs, traffic data, and system files to piece together what happened and how to prevent it from happening again. We specialize in deep-dive analysis using advanced forensic tools and methodologies to uncover hidden threats, determine the extent of data breaches, and identify compromised systems.
Threat Hunting Assessment
Don’t just wait for a cyberattack get ahead of it with EfficienIT’s proactive incident response services. We help businesses stay prepared by enhancing their incident response capabilities and offering expert guidance, training, and regular assessments. This proactive approach helps you spot threats early, reduce investigation costs, and improve your overall security posture. It also protects your reputation and minimizes legal risks, boosting confidence among clients and investors. Stay ahead of cyber threats with EfficienIT’s proactive strategies in Arizona. Contact us today to strengthen your defenses!
Frequently Asked Questions
What’s the difference between digital forensics and incident response?
Digital forensics digs into the details of a cyberattack—finding out what happened, how it happened, and who was behind it. Incident response is about handling the attack as it happens, containing the damage, fixing the problem, and getting everything back to normal.
The Difference Between a Security Incident and a Security Event: A security incident is a confirmed breach or attack that could harm your systems or data, while a security event is any observable occurrence within your network. Not all security events are incidents, but all incidents are events that require action.
EfficienIT provides both digital forensics and incident response services in Phoenix, Scottsdale, and Chandler to help businesses quickly recover and strengthen their defenses.
Why is having an incident response plan so important?
An incident response plan helps you quickly detect and handle breaches, minimizing damage and downtime, and keeping your business running smoothly.
What Are the Key Roles in an Incident Response Plan? Key roles typically include an Incident Response Manager, Security Analysts, Forensics Specialists, and Communications Coordinators. Each role has specific responsibilities to ensure a swift and coordinated response to any cyber threat.
EfficienIT’s incident response services in Arizona help businesses prepare, respond fast, and recover stronger from cyber incidents.
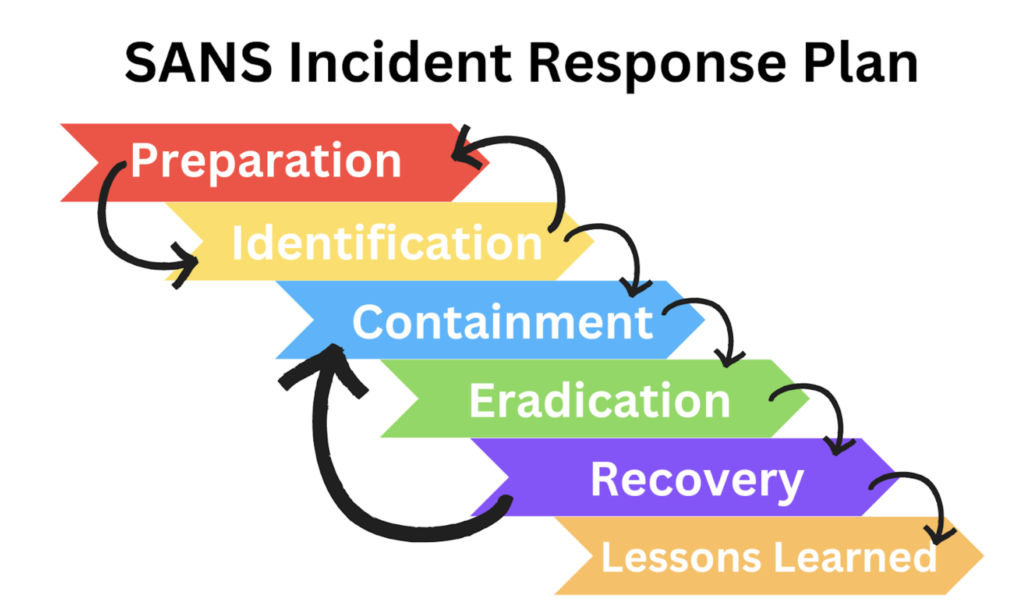
What are the main steps in an incident response plan?
An effective incident response plan usually includes these steps:
- Preparation: Training and readiness for any cyber incident.
- Identification: Spotting and confirming a security threat.
- Containment: Stopping the attack from spreading.
- Eradication: Removing the threat completely.
- Recovery: Restoring systems and operations.
- Lessons Learned: Reviewing the incident to improve future responses.
How Do I Make an Incident Response Plan? Start by assessing your business risks, defining your incident response team and roles, and developing clear procedures for each step. Regular training and updates are crucial to ensure your plan remains effective.
EfficienIT helps businesses in Phoenix, Scottsdale, and Chandler create robust incident response plans tailored to their specific needs, ensuring a quick and effective response to any threats.
How does digital forensics help after a cyberattack?
Digital forensics is crucial for understanding a cyberattack—identifying how attackers breached your defenses, what they accessed, and how to prevent similar incidents in the future. It’s all about gathering and analyzing evidence to understand the full scope of the attack and support legal actions if needed.
At EfficienIT, our forensic experts in Phoenix, Scottsdale, and Chandler conduct thorough investigations to help businesses understand attacks, recover from them, and improve their cybersecurity defenses.
EfficienIT offers comprehensive incident response and forensic services to help Arizona businesses stay ahead of cyber threats and keep their operations secure and efficient. Reach out to us today to learn more!

